How To Use Rootkit Revealer
How to remove or detect a keylogger? If you lot suspect someone stole your password, chances are, it could exist your girlfriend or boyfriend that installed a Keylogger, also known as a rootkit virus. Keyloggers are legal when used according to the constabulary for monitoring your underage children, however, such tools tin be abused for sinister use such as stealing Hotmail and Gmail countersign, not to mention stealing credit carte du jour data.
😭 😍 😂 9 Free Anti-Keyloggers, Keyboard Stroke Scramblers And Virtual Keyboards
What is a rootkit virus? A rootkit for Windows systems is a program that penetrates into the organization and intercepts the system functions ( Windows API ). It can effectively hide its presence by intercepting and modifying low-level API functions. Moreover information technology can hide the presence of particular processes, folders, files and registry keys. Some rootkits install their own drivers and services in the system (they also remain "invisible").
About anti keylogger software are designed to scramble keyboard keystrokes, they are not designed to detect and remove these keylogger software from the system, peculiarly those keyloggers that are securely rooted into the Microsoft Windows Root organisation.
More often than non, keyloggers are known as a very tough to remove spyware reckoner surveillance software in one case it is rooted into the organisation, sometimes they can automatically insert themselves into your antivirus' whitelist, thus making your antivirus ignore them. Yous can try these alternatives.
- v Free Antivirus With 60+ Multi-Engines – Best Antivirus Protection
- xv All-time Complimentary Antivirus 2019 For Windows 10 – Microsoft Defender Alternatives
This is where you lot need a different antivirus software you are currently using, you need a secondary security malware designed to browse and remove rootkit malware such as a keylogger. These standalone anti-malware software are designed from basis upward to scan undetectable rootkits.
Important – These software can only detect and remove software based keyloggers, it does not cease hardware based USB keyloggers that are plugged to your USB keyboard. To stop hardware keylogger, you will demand keyboard scrambler software.
↓ 01 – avast! aswMBR
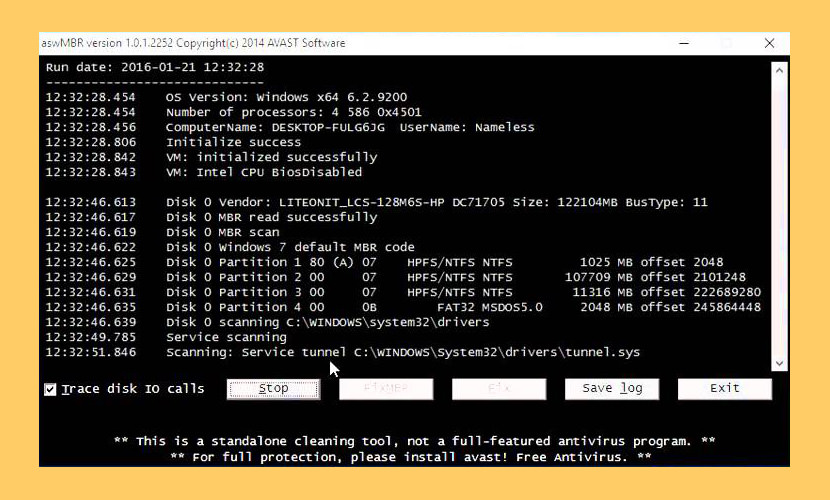
aswMBR is the rootkit scanner that scans for MBR/VBR/SRV rootkits. It tin can discover TDL4/3(Alureon), ZAccess, MBRoot (Sinowal), Whistler, SST, Cidox, Pihar and other malware. The current version of aswMBR uses "Virtualization Technology" to improve detection of stealth malware. Delight notation that to utilise this feature your automobile & CPU must support hardware virtualization.
↓ 02 – GMER
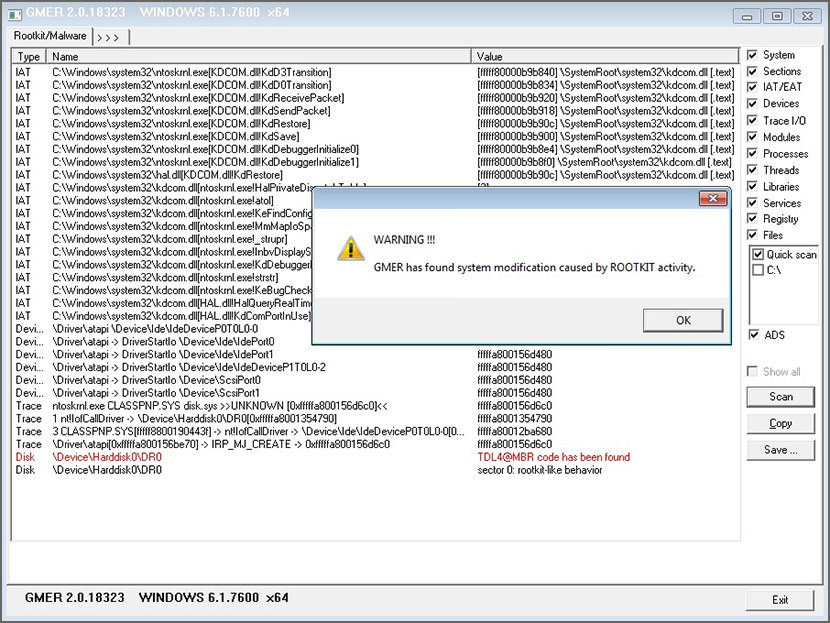
GMER is an application that detects and removes rootkits. It scans for hidden processes, hidden threads, hidden modules, hidden services, hidden files, hidden deejay sectors (MBR), hidden Alternate Information Streams, hidden registry keys, drivers hooking SSDT, drivers hooking IDT, drivers hooking IRP calls and inline hooks.
↓ 03 – Kaspersky Lab TDSSKiller
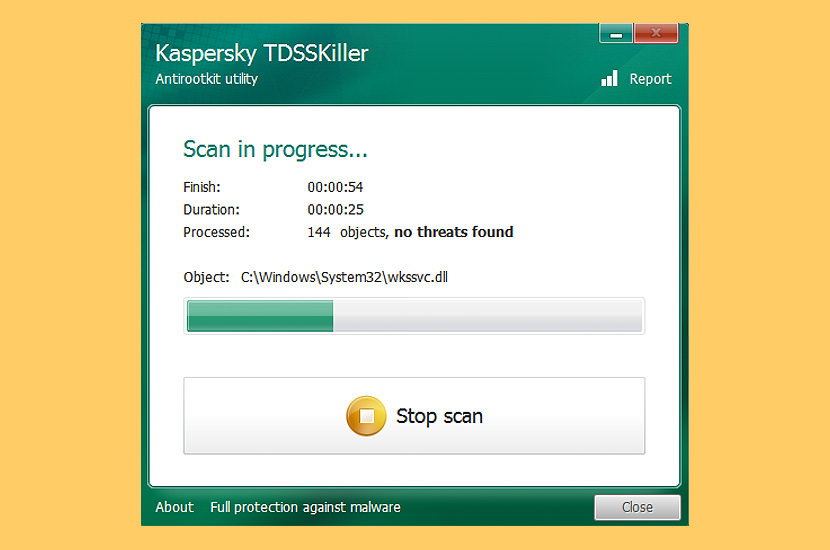
Developed by Kaspersky Lab, TDSSKiller is a Gratis handy tool that can quickly discover and remove both known and unknown rootkits, which are programs that can hide the presence of malware in your organization. A rootkit for Windows systems is a programme that penetrates into the system and intercepts the organization functions (Windows API).
It tin can effectively hide its presence by intercepting and modifying low-level API functions. Moreover it can hide the presence of particular processes, folders, files and registry keys. Some rootkits install its own drivers and services in the system (they also remain "invisible"). The TDSSKiller utility detects and removes the post-obit malware:
- Malware family unit Rootkit.Win32.TDSS;
- Bootkits;
- Anti-Keylogger
- Rootkits
Listing of malicious programs: Rootkit.Win32.TDSS, Rootkit.Win32.Stoned.d, Rootkit.Boot.Cidox.a, Rootkit.Kick.SST.a, Rootkit.Kicking.Pihar.a,b,c, Rootkit.Boot.CPD.a, Rootkit.Boot.Bootkor.a, Rootkit.Boot.MyBios.b, Rootkit.Win32.TDSS.mbr, Rootkit.Boot.Wistler.a, Rootkit.Win32.ZAccess.aml,c,eastward,f,k,h,i,j,k, Rootkit.Kicking.SST.b, Rootkit.Boot.Fisp.a, Rootkit.Kick.Nimnul.a, Rootkit.Boot.Batan.a, Rootkit.Boot.Lapka.a, Rootkit.Boot.Goodkit.a, Rootkit.Boot.Clones.a, Rootkit.Boot.Xpaj.a, Rootkit.Boot.Yurn.a, Rootkit.Kicking.Prothean.a, Rootkit.Boot.Plite.a, Rootkit.Boot.Geth.a, Rootkit.Boot.CPD.b, Backstairs.Win32.Trup.a,b, Backstairs.Win32.Sinowal.knf,kmy, Backdoor.Win32.Phanta.a,b, Virus.Win32.TDSS.a,b,c,d,due east, Virus.Win32.Rloader.a, Virus.Win32.Cmoser.a, Virus.Win32.Zhaba.a,b,c, Trojan-Clicker.Win32.Wistler.a,b,c, Trojan-Dropper.Boot.Niwa.a, Trojan-Ransom.Boot.Mbro.d, due east, Trojan-Ransom.Boot.Siob.a, Trojan-Ransom.Boot.Mbro.f.
↓ 04 – Malwarebytes Anti-Rootkit Beta
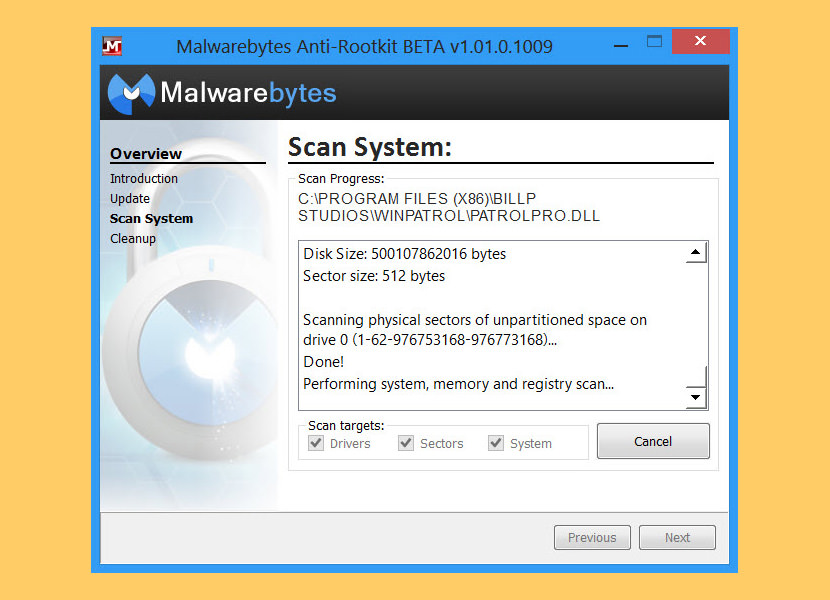
Malwarebytes Anti-Rootkit BETA drills downward and removes even securely embedded rootkits. Malwarebytes Anti-Rootkit BETA is cutting border technology for detecting and removing the nastiest malicious rootkits. Removes and repairs the latest rootkits and the damage they cause.
↓ 05 – Intel'due south McAfee RootkitRemover

McAfee RootkitRemover is a stand-solitary utility used to detect and remove complex rootkits and associated malware. Currently it can detect and remove ZeroAccess, Necurs and TDSS family of rootkits. McAfee Labs plans to add together coverage for more rootkit families in future versions of the tool.
↓ 06 – Norton Power Eraser
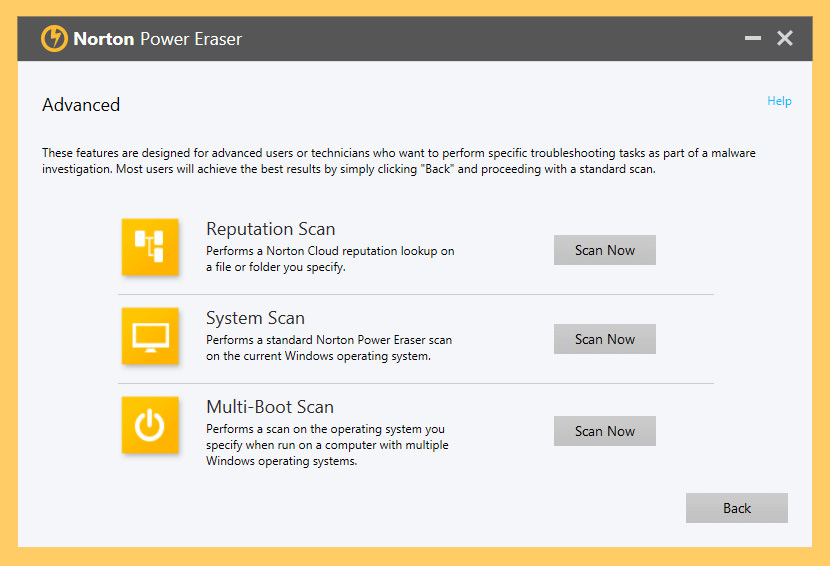
Norton Power Eraser uses our near aggressive scanning engineering to eliminate threats that traditional virus scanning doesn't always notice, so you can become your PC back. Because Norton Power Eraser is an ambitious virus removal tool, it may mark a legitimate program for removal. However, y'all can always disengage the results of a browse. Information technology tin also assistance detect and remove Potentially Unwanted Programs. Possibly the best free rootkit scanner and remover.
↓ 07 – Trend Micro RootkitBuster
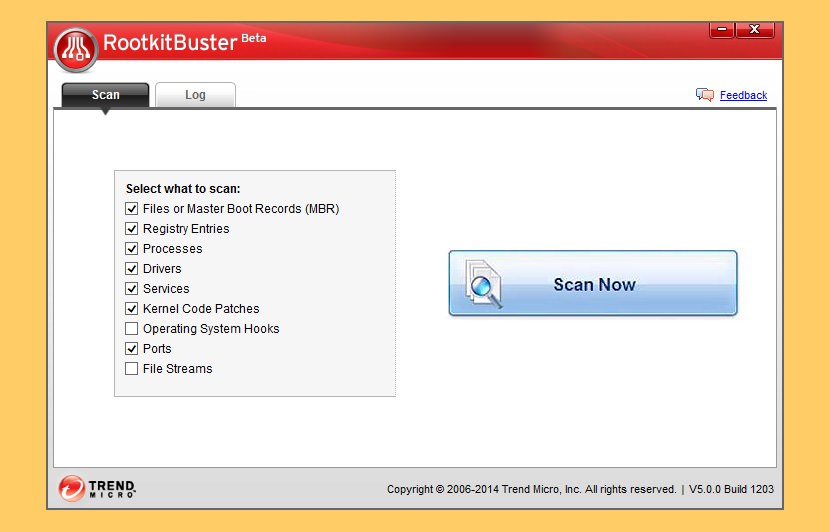
Malicious software called rootkits can manipulate the components of the Microsoft Windows operating system to conceal how they cause harm. Rootkits can hide drivers, processes, and registry entries from tools using common organization application programming interfaces (APIs). Tendency Micro RootkitBuster scans hidden files, registry entries, processes, drivers, services, ports, and the principal boot record (MBR) to identify and remove rootkits.
↓ 08 – UnHackMe | Free xxx Days
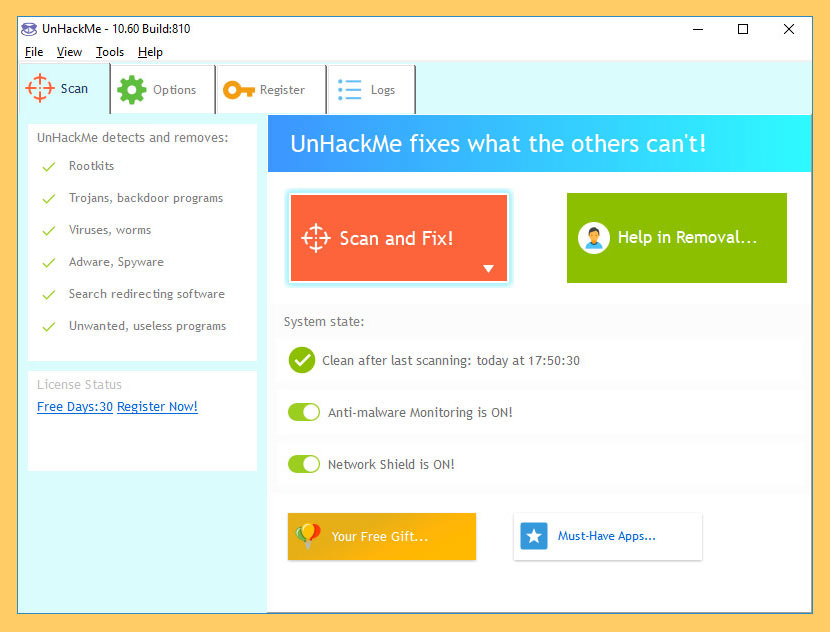
UnHackMe was initially created as anti-rootkit software (2005), merely currently eliminates the following types of malicious software – Search redirecting, Popup ads, Potentially unwanted programs (PUPs), Unwanted processes, Tiresome browsing, Rootkits, Trojans, Spyware, Keyloggers and etc. UnHackMe uses its own database to detect which programs you lot should remove from your PC. You can agree with it or not. If you notice a plan on the list that is OK, you can marker information technology as a False Positive.
- Scanning of installed programs for "Potentially Unwanted Programs" (PUPs).
- Checking for junk files, created by PUPs, adware, and spyware.
- Scanning of Windows startup programs, services, and drivers.
- Testing Windows shortcuts.
- Scanning for rootkits.
- Examining browsers search settings.
- Scanning browsers add together-ons.
- Testing the hosts file and DNS settings.
- Testing startup files using several antivirus programs on Virustotal.com.
↓ 09 – AntiSpy
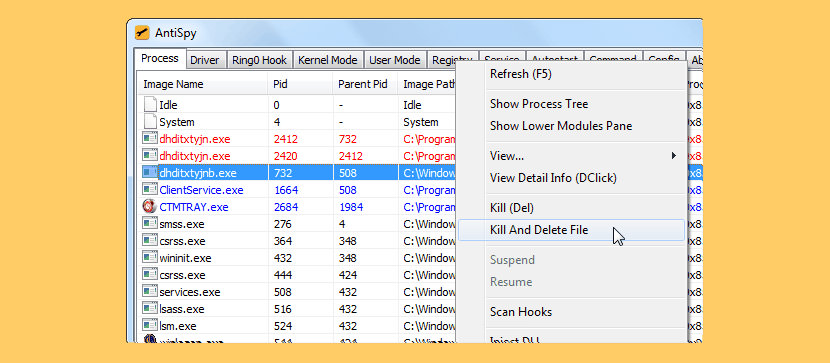
AntiSpy is a free but powerful anti virus and rootkits toolkit.Information technology offers you the ability with the highest privileges that can detect,analyze and restore diverse kernel modifications and hooks.With its help,you can easily spot and neutralize malwares subconscious from normal detectors.
↓ 10 – NoVirusThanks Anti-Rootkit
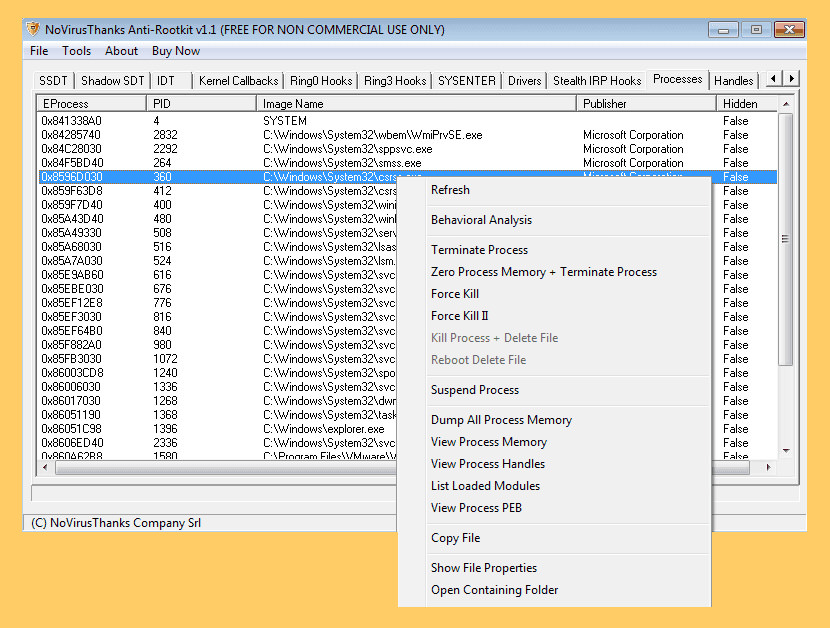
NoVirusThanks Anti-Rootkit is a sophisticated depression-level system assay tool whose chief goal is to detect the presence of malware and rootkits. Hidden processes, subconscious drivers, stealth DLL modules, code hooks etc. are just a few of the objects which can exist detected in user infinite and organisation memory.
NoVirusThanks Anti-Rootkit detect undetectable stealth malware is a must-accept for anyone seeking true 32-bit Windows NT kernel security and arrangement threat assay. The vast detection range of manufacture standard rootkits is truly amazing especially without compromising system stability fifty-fifty in the virtually hostile, malware-plagued environments.
It is recommended to use this software by experienced users. NoVirusThanks Anti-Rootkit is fully compatible with the following 32-bit Microsoft Windows Operating Systems: Windows XP, Windows Server 2003, Windows Vista, Windows Server 2008, Windows Server 2012, Windows 7
↓ 11 – USEC RADIX
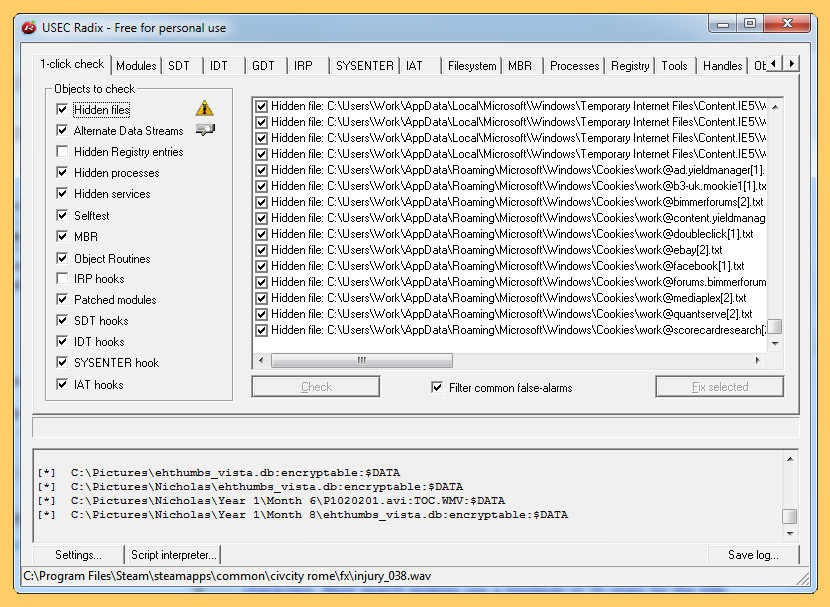
Rootkits are dangerous programs that are downloaded from the Internet, or nowadays in malicious purchased software, that once installed take over your figurer without your knowledge. Rootkits can exercise anything from logging every ane of your keystrokes, including usernames and passwords, electronic mail messages or even your discussion processing documents and sending that information off to hackers, to executing programs in the groundwork without your knowledge or permission.
And in that location's nix that you tin do most it unless you lot accept the time right now to install Radix. It's your all-time hope confronting combating Rootkit Attacks. Hither's what Radix does…
- Detects and removes Rootkits using sophisticated methodologies.
- Detects and repairs drivers that accept been modified past Rootkits.
- Detects and repairs computer processes modified by Rootkits.
- Detects and reveals hidden processes and files, including Alternate Information Streams (ADS).
- Allows the removal of "locked" or "unremovable" processes and files.
- Provides to dump retention areas from processes.
- Shows the Global Descriptor Table (GDT) for advanced Rootkit Detection capabilities.
- Shows the Import Accost Table (IAT) for avant-garde Rootkit Detection capabilities.
- Shows the Interrupt Descriptor Table (IDT) for advanced Rootkit Detection capabilities.
- Shows subconscious Registry Keys.
- Operates in both command line way for power users, or as a graphical tool for regular users.
↓ 12 – Sophos Virus Removal Tool
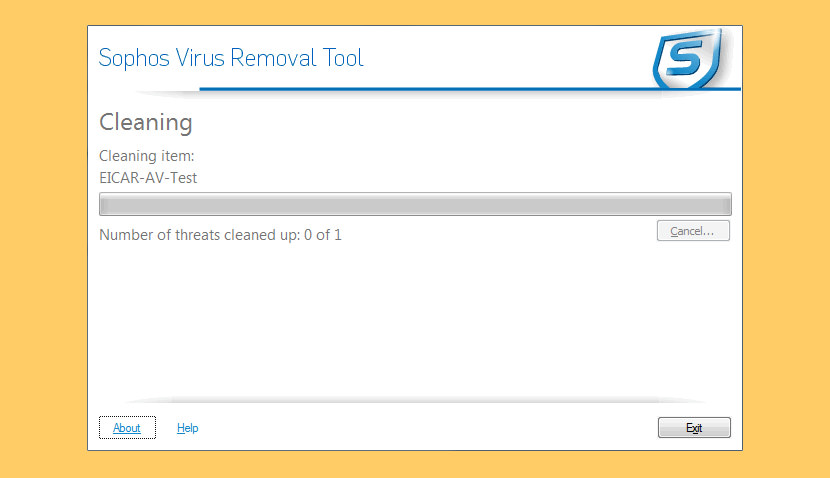
Sophos Virus Removal Tool scans, detects, and removes whatsoever rootkit that is hidden on your computer using avant-garde rootkit detection technology. Rootkits tin lie hidden on computers and remain undetected by antivirus software.
Although new rootkits can be prevented from infecting the arrangement, whatsoever rootkits present before your antivirus was installed may never exist revealed. Sophos Virus Removal Tool will scan your reckoner and let you lot safely and reliably observe and remove any rootkit that might have subconscious itself on your system.
- User memory scanning and cleaning
- Kernel retentiveness scanning and cleaning
- File scanning
↓ 13 – Emsisoft Emergency Kit
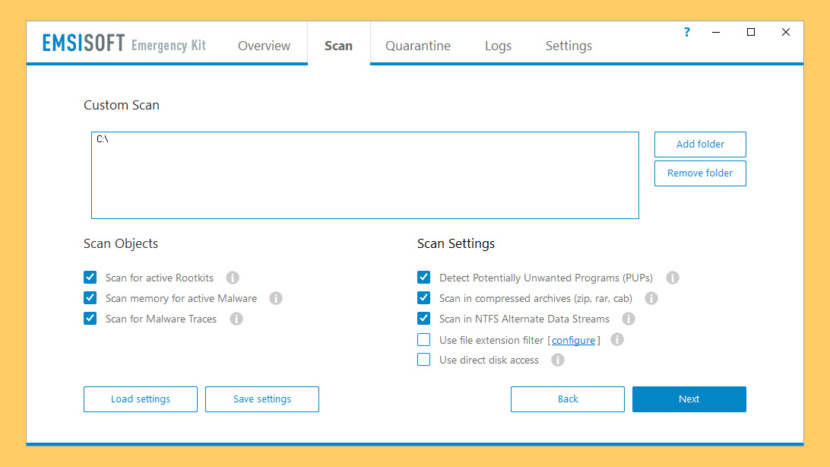
The Emsisoft Emergency Kit Scanner includes the powerful Emsisoft Scanner complete with graphical user interface. Scan the infected PC for Viruses, Trojans, Spyware, Adware, Worms, Dialers, Keyloggers and other malicious programs. The scanner contains the same functionality as the Emergency Kit Scanner but without a graphical user interface. The command line tool is fabricated for professional users and is perfect for batch jobs. Very skillful at detecting spyware and removing keyloggers.
- Malware detection – Features the complete dual-scanner technology of Emsisoft Anti-Malware, with millions of signatures for all types of online threats.
- Removal – Thorough quarantine or removal of detected objects with saving of log files.
- Portable – Fully portable solution, no installation required.
- Updates – Self updating with but one click. All software updates included for a year.
↓ 14 – Microsoft RootkitRevealer
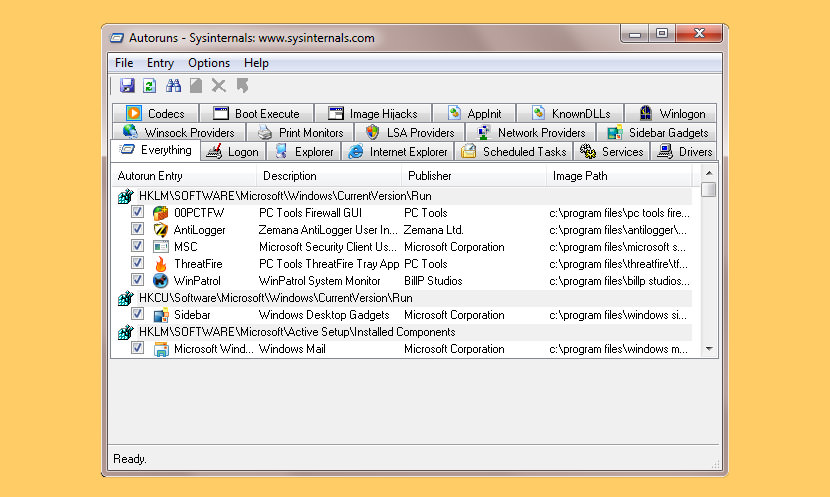
RootkitRevealer is an advanced rootkit detection utility. Information technology runs on Windows XP (32-bit) and Windows Server 2003 (32-scrap), and its output lists Registry and file arrangement API discrepancies that may indicate the presence of a user-mode or kernel-mode rootkit. RootkitRevealer successfully detects many persistent rootkits including AFX, Vanquish and HackerDefender (note: RootkitRevealer is not intended to notice rootkits like Fu that don't try to hide their files or registry keys). If y'all use it to place the presence of a rootkit please allow us know!
The reason that there is no longer a command-line version is that malware authors have started targeting RootkitRevealer's browse by using its executable name. We've therefore updated RootkitRevealer to execute its scan from a randomly named copy of itself that runs as a Windows service. This blazon of execution is not conducive to a control-line interface. Note that you tin can utilise command-line options to execute an automatic scan with results logged to a file, which is the equivalent of the command-line version's beliefs.
↓ xv – SpyShelter Anti Keylogger | Gratuitous 14 Days
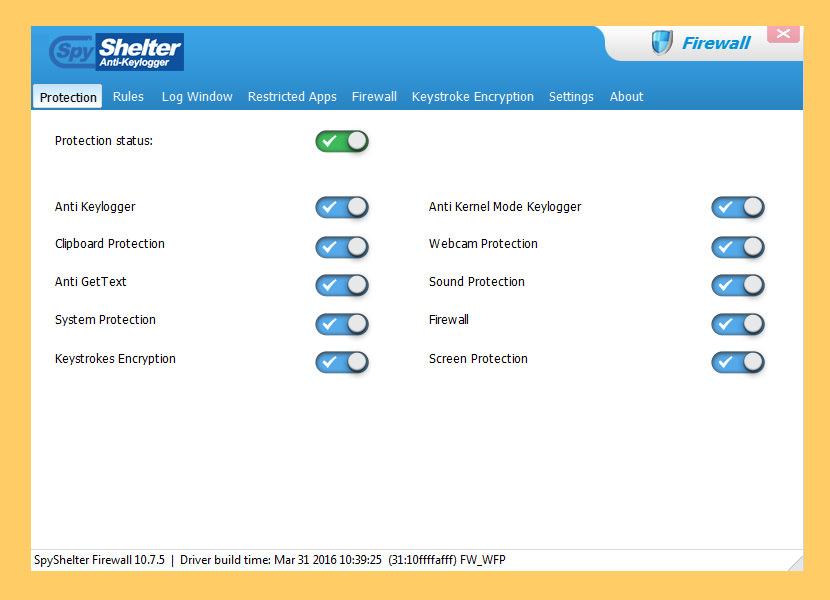
SpyShelter Anti Keylogger provides solid protection in existent time against known and unknown "zip-day" spy and monitoring software, for example: keyloggers, screen loggers, webcam loggers, and even advanced financial malware. SpyShelter Anti Keylogger monitors behavior of all currently ongoing actions on your PC and allows you to prevent any action that malware attempts to brand.
Cheers to our unique engineering, SpyShelter is capable of stopping both commercial and custom-made keyloggers, which cannot exist detected by any anti-virus software. Since SpyShelter does not rely on whatever fingerprint database, you lot volition non have to worry about zero-solar day malware – your registry, RAM and all applications are going to be protected from the moment yous install SpyShelter.
- Protect yous against stealing your individual information like passwords, chat messages or credit card data.
- Detect and stop dangerous avant-garde null-mean solar day malware.
- Allow you to define rules for every awarding. Y'all are in charge of your PC.
- Encrypt keystrokes of all applications on kernel level.
- Protect your webcam and microphone confronting hijacking.
↓ 16 – Spy DLL Remover
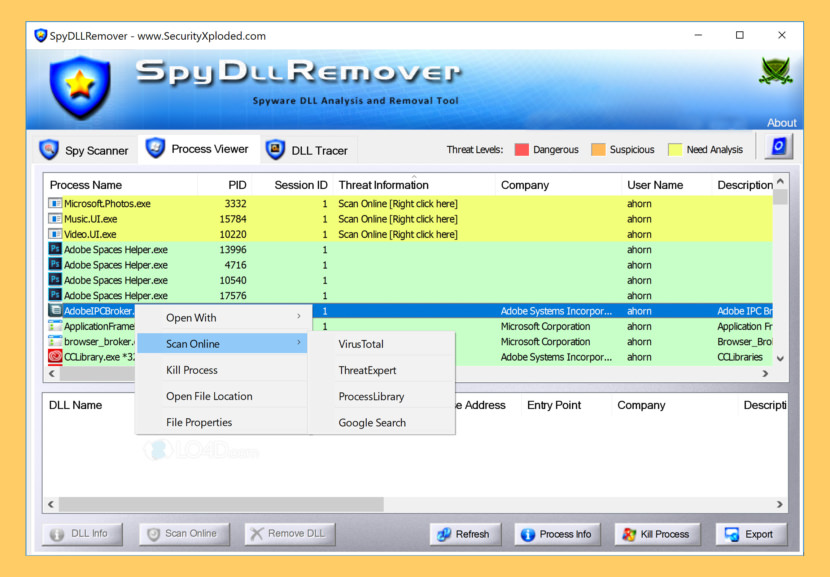
SpyDllRemover is the specialized tool for detecting Spyware & Hidden Rootkit Dlls in the System. In improver to Spyware Dlls, it tin can also find user-land Rootkit processes using multiple Anti-Rootkit techniques. Information technology uses Heuristic analysis and 'Online Threat Verification' for deeper analysis of unknown Malware Threats.
- Advanced Spyware Scanner: Detects Hidden User-state Rootkit processes as well every bit suspicious/injected Dlls within running Processes.
- Hidden Rootkit Detection & Removal: Uses multiple techniques to detect user-country Rootkits such equally Direct NT System Call Implementation, Process ID Beast force Method (PIDB) as first used by BlackLight, and CSRSS Process Handle Enumeration Method.
- Unique 'Avant-garde DLL Ejection': This is one of the Advanced & Unique characteristic of SpyDLLRemover used to completely remove the injected DLL from Remote Procedure.
- Sophisticated Auto Assay: Dll & Process Heuristics to aid in Identification of known as well as Unknown Threats.
↓ 17 – RKill
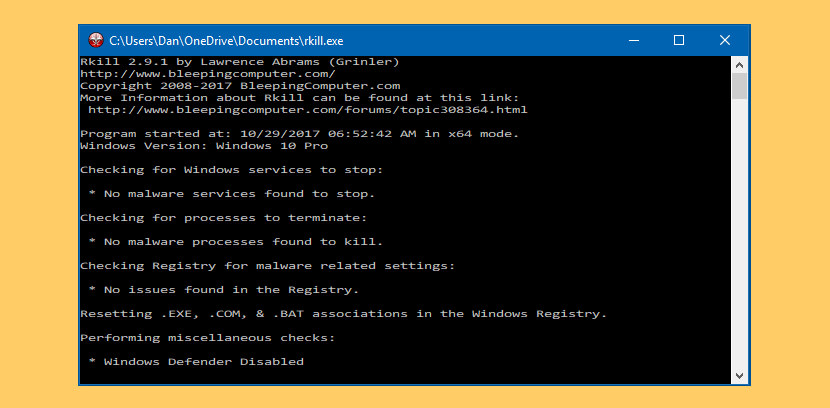
RKill is a program that was developed at BleepingComputer.com that attempts to cease known malware processes so that your normal security software tin then run and make clean your estimator of infections. When RKill runs it will kill malware processes and then remove incorrect executable associations and ready policies that stop us from using certain tools. When finished it volition display a log file that shows the processes that were terminated while the programme was running.
↓ 18 – SuperAntiSpyware Free
Protect your PC from malicious threats from malware, spyware, trojans, and more. SUPERAntiSpyware specializes in unique and difficult-to-find malware, identifying and removing instances of malicious threats including Spyware, Adware, Trojans, Worms, Ransomware, Hijackers, Parasites, Rootkits, KeyLoggers, and more than.
Protect your figurer from threats: spyware, adware, trojans, ransomware, PUPs, hijackers, and more than. Get the most upwards-to-engagement protection with database updates 2-4x a twenty-four hour period and in-depth system scanning and removal tools. Install our lightweight programme that won't slow downward your PC, and works with, not against, your antivirus.
↓ 19 – Bitdefender Rootkit Remover [ Discontinued ]
The Bitdefender Rootkit Remover deals with known rootkits quickly and finer making use of accolade-winning Bitdefender malware removal technology. Dissimilar other like tools, Bitdefender Rootkit Remover can be launched immediately, without the need to reboot into safe mode first (although a reboot may be required for complete cleanup).
Rootkit Remover deals easily with Mebroot, all TDL families (TDL/SST/Pihar), Mayachok, Mybios, Plite, XPaj, Whistler, Alipop, Cpd, Fengd, Fips, Guntior, MBR Locker, Mebratix, Niwa, Ponreb, Ramnit, Stoned, Yoddos, Yurn, Zegost and also cleans infections with Necurs (the concluding rootkit standing). Both x86 and x64 Rootkit Remover kits are available, please cull the appropriate one for your system.
↓ twenty – PCHunter anti-rootkit [ Discontinued ]
PCHunter anti-rootkit is a free and handy toolkit for Windows with various powerful features for kernel structure viewing and manipulation. It offers you the ability with the highest privileges to find, analyze and restore various kernel modifications and gives you a broad scope of the kernel. With its assist, you can easily spot and neutralize malwares hidden from normal detectors.
Conclusion
Accept circumspection when opening attachments: Keyloggers tin can exist nowadays in files received through electronic mail, chats, P2P networks, text messages or fifty-fifty social networks. If someone sends you an email out of the cold or the contents of the e-mail are asking for your personal information, chances are at that place'south a keylogger in there somewhere.
How to remove rootkit virus? Where to download free rootkit detection and removal software? A rootkit virus, trojan, spyware and worm is a malware plan that has administrator level access to all the network systems. What it does is it burrows itself deep into the arrangement and hides itself, making information technology almost invisible and hard to be removed and detected by antivirus.
Usually rootkit malware monitor traffic, keystroke and allow backstairs access for spreading viruses and trojans, some even turn your computer into a botnet – a term known as sending out spam mail via your reckoner without you lot always knowing.
It is hard for normal antivirus to detect their presence because rootkit tends to boot up along with windows before the antivirus is booted up. Near antivirus at present comes with rootkit detector and detection ability, not to mention the ability to remove these rootkits, all the same, if the rootkit malware is present prior to the installation of the new antivirus, and so it is not possible for the antivirus to detect information technology.
How To Use Rootkit Revealer,
Source: https://www.geckoandfly.com/17960/anti-keylogger-rootkit-detection-and-removal-for-undetectable-spyware-computer-surveillance-malware/
Posted by: glessnersopland.blogspot.com


0 Response to "How To Use Rootkit Revealer"
Post a Comment